Workday’s native security and control features require a paradigm shift from traditional approaches to security.
Workday operates on a single security model where access to data is limited to the application. Everyone, including end users, integration security users (ISUs), mobile device users, and IT support must authenticate through the single security model. In contrast, legacy systems provide different access points (i.e., the application layer, database layer, etc.) requiring different considerations to secure and protect data.
Why Security Is Important
Users with excessive access or conflicting duties increase the risk of erroneous transactions, fraudulent activity, or information leakage. Moreover, users with multiple duties to configure security, grant access, modify system configuration settings, and carry out business transactions increase the risk that application controls dependent upon configuration settings could be circumvented.
Most organizations must comply with regulations concerning security such as SOX, MAR, GDPR, HIPAA, and more, making tight controls paramount.
Security and Compliance Duties and Obligations
Workday provides the ability to monitor, audit, and report on the health of all security-related transactions within the Workday tenant. The challenge is that there is so much data in so many places and multiple ways to access it. It can be overwhelming.
Organizations should ensure that:
- Access is limited to “need to know.”
- Proper segregation of duties is in place.
- Administrative access is restricted to authorized individuals.
- ISUs are configured securely.
- Appropriate authentication policies are in place to restrict system access inclusive of multi-factor authentication (MFA) and SAML single sign on (SSO) setup and configuration.
- Tenants are logically separated.
- Data is protected and masked were deemed necessary.
How CrossVue Can Help
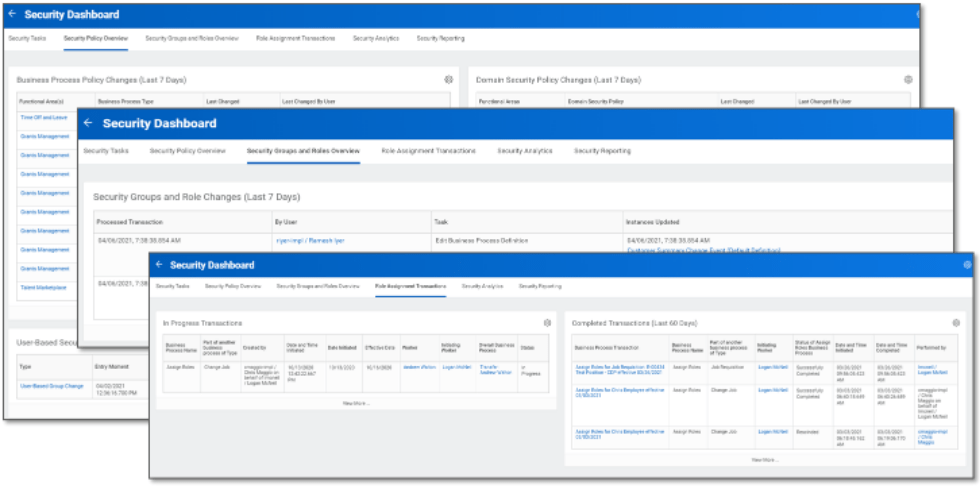
CrossVue’s custom-built Security Dashboard is intended to support organizations with their day-to-day responsibilities through an improved experience.
- Transactional monitoring and tracking can be accomplished via the Security Policy Overview and Security Groups and Roles Overview tabs. Reviewing Role Assignment Transactions is done all in one place. Additionally, administrators can easily provide systems and user maintenance as well as maintain proxy and authentication policies.
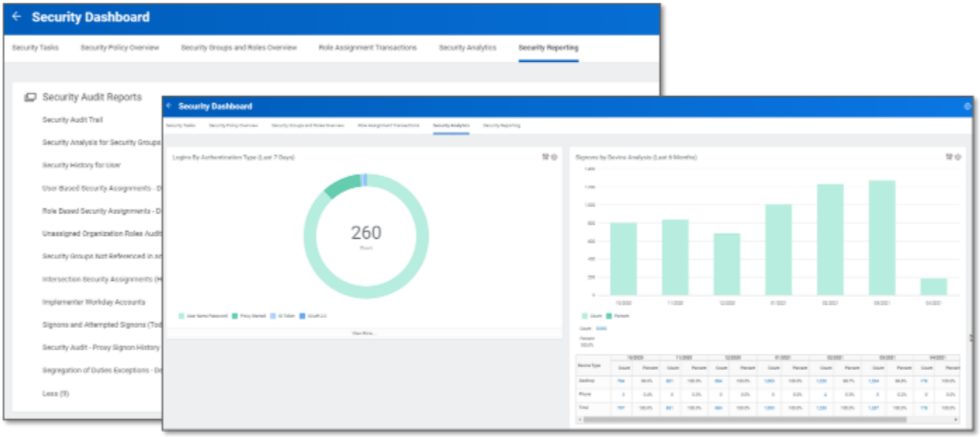
- The Security Reporting tab includes key system reports to monitor and support the security landscape including Security Reporting, Auditing, and Analytics.
Workday Next Steps
Start with the below recommended next steps and activities:
- Assess authentication policies configured in Workday.
- Configure security dashboards into the Workday production tenant to report on security group and user access data into a security matrix that can be imported into Excel.
- Lead “workshop” meetings to identify users whose access is more than what is required for their job duties or may present a segregation of duties conflict.
- Discuss preliminary user access and SOD issues and risks with stakeholders and make formal recommendations to enhance Workday security.
- Understand and evaluate the process for granting, approving, removing, and monitoring Workday user access.
- Ensure ISU accounts are appropriately restricted and configured.
- Identify where sensitive data resides and activate data masking where appropriate.
For expert support implementing maximum Workday security and data protection controls, contact CrossVue today.


